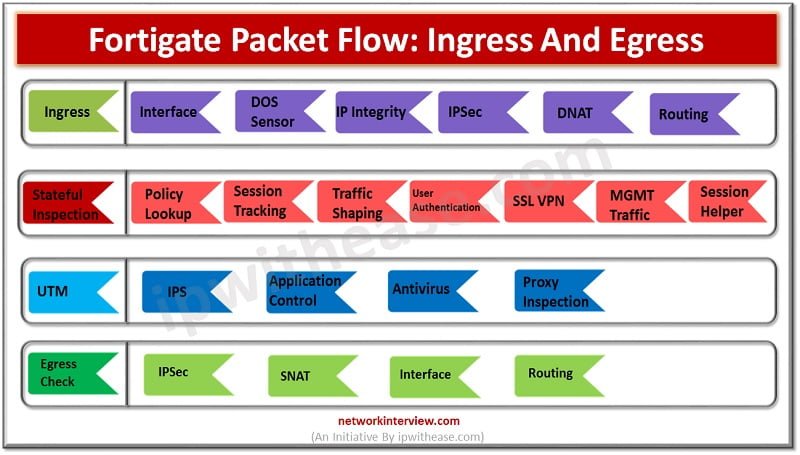
What comes first on FortiGate: routing or security actions?
In this case, the destination is more important than the journey.

Today's article is very brief but is something that warrants attention. It starts with a deceptively simple question: when a FortiGate firewall receives network traffic on an interface, what comes next – routing or security actions?
While it's tempting to consider security actions as the immediate next step, it's actually routing. That's right: routing takes place before nearly all security features on the FortiGate. This includes security functions like:
- Policy evaluation
- Deep packet inspection
- Source NAT (SNAT)
Another way to think of it: most FortiGate security functions have a dependency on outgoing interfaces. The firewall needs to know what local interface the traffic would try to leave through before it can decide what security measure to take.
Easy peasy right? For additional info and reference, check out these docs: