What are the antivirus scanning techniques that FortiGate can perform?
Reviewing the various ways a FortiGate can scan files for viruses.

💡
This is part of an on-going series in cybersecurity foundations. Check the cyber 101 article tag index from time to time for more content.
Antivirus scanning at a firewall level has been around for quite awhile. Over time though, the specific techniques to identify threats have changed and evolved. Here's a breakdown of the common techniques that a FortiGate firewall can perform during a virus scan:
- Signature-based detection - This is one of the most common techniques and essentially just compares a file signature with a known virus database maintained by FortiGuard Labs.
- Content Disarm and Reconstruction (CDR) - This is a technique where active content/media is removed from certain files (e.g. Office, OpenOffice, PDF, etc) leaving just the text in place when the user gets the file.
- Virus Outbreak Prevention (VOS) - This is also signature based but leverages third-party signatures from FortiGuard's extended Global Threat Intelligence database. It's optional but the benefit here is that additional threats observed outside of Fortinet could be protected.
- Zero-day malware stream scanning - This is a feature that basically allows the FortiGate to receive a steady stream of malware IOCs via partnership with the FortiSandbox product/license.
- External Malware Block List - This allows the FortiGate to use an external malware blocklist specified by the firewall admin themselves.
- EMS Threat Feed - This allows the FortiGate to block threats identified by the FortiClient EMS system.
- Behavior-based Detections - This allows the firewall to submit/offload suspicious files to FortiSandbox (separate product) for analysis.
- CIFS Scanning - This is just basic file type filtering. It's helpful for reducing attack surface if you know that specific types files (scripts, executables, etc) never need to be downloaded/transported for users.
- Heuristic Analysis - This is a feature which uses machine learning models from FortiGuard to identify suspicious/malicious characteristics in files. Things like questionable content/structure in portable executable files, etc.
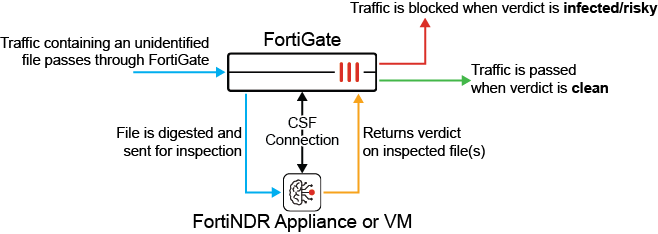
- Behavioral and Human Analysis - This is more of a feature/functionality of FortiNDR but I'm mentioning it as it's referenced in the documentation. In this workflow, the FortiGate essentially offloads a file for inspection to a FortiNDR appliance/VM for scanning.
For more information, check out these resources:
Antivirus techniques | Administration Guide

Testing an antivirus profile | Administration Guide

CIFS support | Administration Guide

Using FortiNDR inline scanning with antivirus | Administration Guide